Sign-In and Security
The Sign-In and Security section is crucial for safeguarding a user’s account while ensuring a seamless and secure sign-in process. This section primarily focuses on how users authenticate and access their accounts, as well as the various security mechanisms in place to protect sensitive data and prevent unauthorized access.
In this section, users can manage their sign-in preferences, security settings, and monitor any recent security activity related to their account. It encompasses elements such as two-factor authentication (2FA), password management, trusted phone numbers, and other security protocols to ensure that the account remains safe from unauthorized access or breaches.
1. Core Features of Sign-In and Security
Contact Info: Email and Phone
Email: The email address is a fundamental part of the user's account. It is used for account identification and communication. In this section, users can view their email address but cannot update it. This ensures that the account's primary communication channel is secure and consistent.
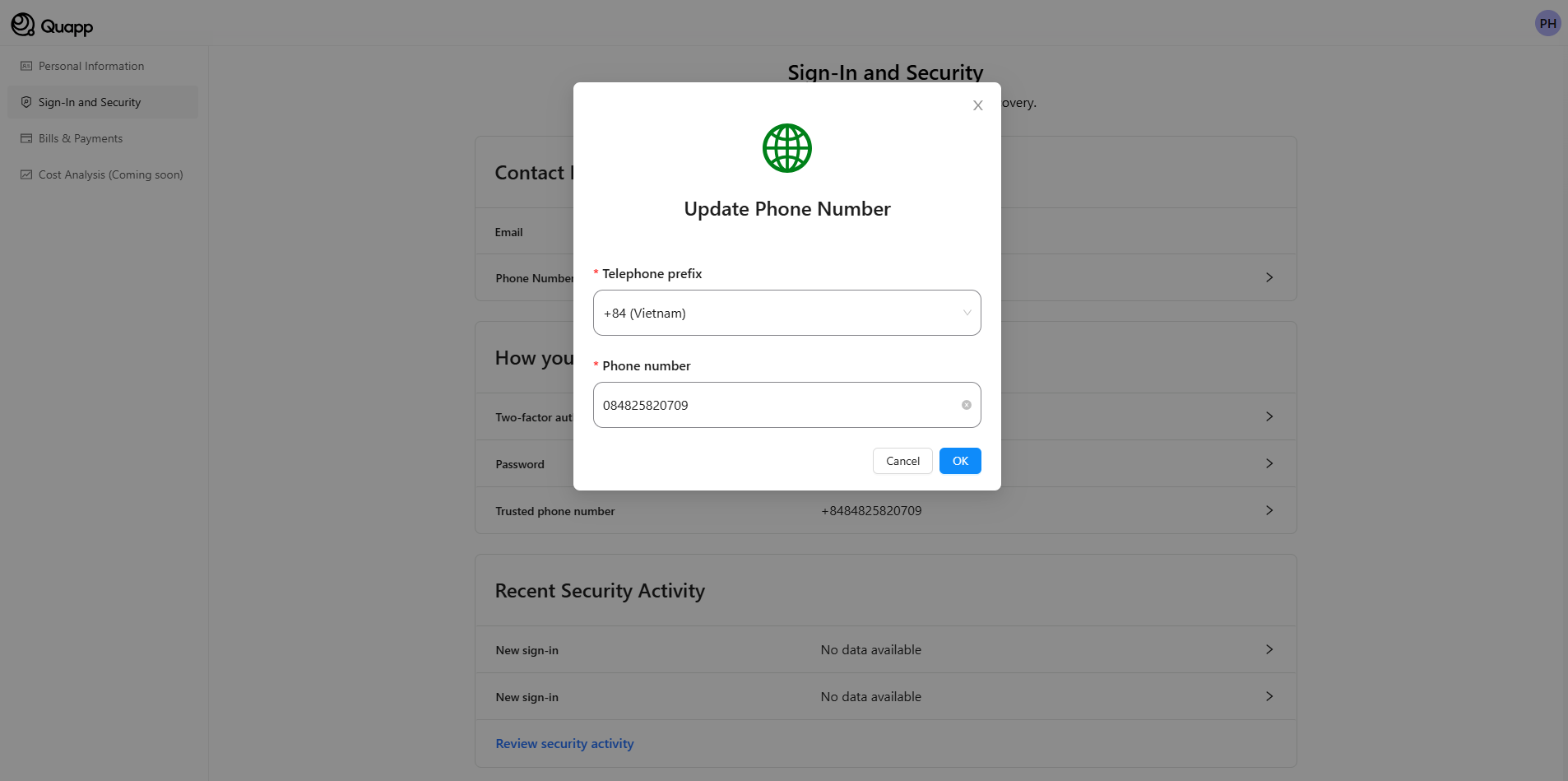
Phone: Users are able to view and update their phone number. A phone number is often associated with security features like two-factor authentication (2FA) and is used to verify the identity of the user when they log in, reset passwords, or perform sensitive actions on their account. Updating a phone number is a key part of maintaining the security of the account.
Two-Factor Authentication (2FA)
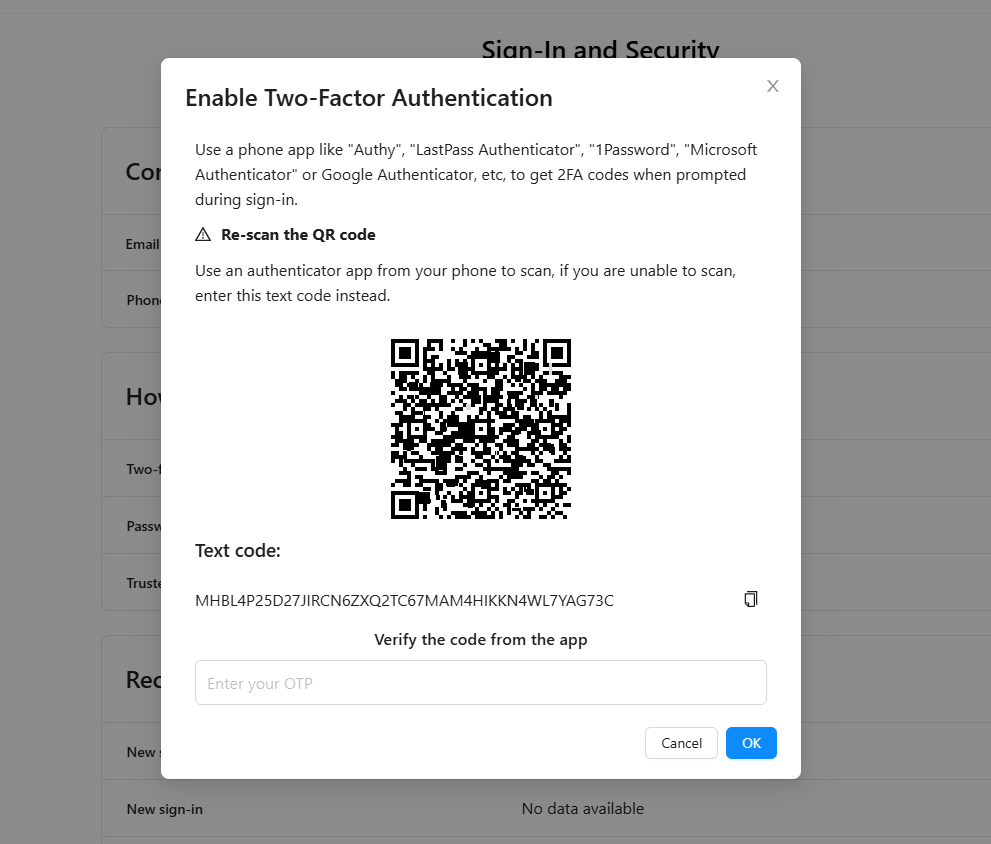
Purpose: Two-factor authentication adds an extra layer of security to the user's account. Even if someone else knows the user’s password, they cannot access the account without the second factor of authentication, which is usually a code sent to a trusted device (such as a phone or email).
How It Works: When enabled, users are required to provide both their password and a verification code that is sent to their phone or email each time they log in. This ensures that only the account owner can access the account, even if the password is compromised.

Activation and Configuration: Users can enable or disable 2FA in this section. They can choose between different methods for receiving the second factor, such as via SMS, an authenticator app (e.g., Google Authenticator), or email.
Password Management
- Changing Passwords: Users can change their password in this section. A strong password is an essential aspect of account security. It is recommended that passwords be updated periodically, especially if the user suspects that their account might have been compromised.
- Password Recovery: If a user forgets their password, they can initiate a recovery process. This typically involves receiving a password reset link or code through their registered email or phone number to regain access to their account.
- Password Strength and Guidelines: The system may include password strength requirements (e.g., length, character types) to ensure users create secure passwords that are difficult to guess or crack.
Trusted Phone Number
- Purpose: The trusted phone number is used to further secure the account. It can serve as a second line of defense when users log in or perform sensitive actions. For example, it might be used for 2FA or as part of a recovery process when access is needed.
- Updating and Verification: Users can add, verify, and remove trusted phone numbers. If a user adds a new phone number, they will typically need to verify it by entering a code sent to that number.
Recent Security Activity
- Monitoring Account Activity: This section allows users to review recent security-related events or actions on their account. This could include logins from new devices, password changes, or successful/failed attempts to access the account.
- Alerts and Notifications: Users receive alerts via email or through the app if suspicious activities are detected, such as login attempts from unusual locations or devices. This helps users stay aware of any unauthorized attempts to access their account and take immediate action, such as changing their password or enabling 2FA.
2. Security Measures and Best Practices
Account Lockout After Multiple Failed Attempts: To prevent brute-force attacks, the system locks out the account after a certain number of failed login attempts. This helps to deter attackers from guessing passwords or bypassing security measures.
Email and Phone Verification: Regular verification of email and phone numbers ensures that the account’s contact information remains up to date and secure. If any changes are made to these details (such as changing the phone number), a verification code is sent to the old phone or email to confirm the changes.
Session Management: Enables users to monitor and manage all active sessions associated with their account. This functionality helps users identify any unauthorized or unnecessary active sessions and log out from devices or browsers they don’t recognize.
Security Alerts and Notifications: Users are notified about key security events, such as login attempts from new devices or locations, changes in account settings, or other suspicious activities. This proactive approach to security keeps users informed and helps mitigate risks.
Encryption and Data Protection: All sensitive data, including passwords, phone numbers, and authentication tokens, is securely encrypted to protect user privacy and prevent unauthorized access.
User Education and Recommendations: The system may offer tips and recommendations for improving account security, such as using a password manager, enabling 2FA, or avoiding easily guessable passwords. Educating users on security best practices ensures that they take appropriate steps to protect their accounts.
3. Why Sign-In and Security Matter
Prevent Unauthorized Access: The security measures ensure that only the rightful user can access the account, protecting sensitive data and preventing misuse.
Protection Against Phishing and Fraud: By requiring two-factor authentication and secure password management, users are less likely to fall victim to phishing scams or unauthorized access.
Peace of Mind: Knowing that the account is protected by robust security features allows users to interact with the platform with confidence, without worrying about potential breaches.